When I started thinking about this post, my initial thought was discussing trust as the foundation to our security success, building on our CEO Tim Moore’s post. Taking a step back, I realized the opposite was true – a lack of trust is our true foundation, because trust is only earned through holistic security culture and practices.
Described as the internet’s first killer app, email is in many ways society’s connective tissue. It’s still the most ubiquitous and relied-upon mechanism for digital communication, with Statista predicting 4.73 billion global users by 2026. Yes, billion with a big ol’ B.
Over time, email has become a cat and mouse game between malicious actors like those pesky Nigerian scammers and a myriad of service providers (including SocketLabs, ESPs like SendGrid, anti-abuse partners like Spamhaus, and mailbox providers like Google and Yahoo), each contributing their own piece of the internet’s infrastructure. Within this, the global technology industry has become acutely aware of the potential risks with sharing personally identifiable information (PII).
To support email as a safe and reliable global thread, we need concerted collaboration throughout the industry to imagine enhanced security protocols to thwart the malicious cat chasing our mouse-like email users.
This was certainly not lost on SocketLabs’ founder, John Alessi, who created and instilled a culture of security and compliance some (even me, at times) considered extreme. Though, as I continue to witness the relentless barrage of security breaches and the advanced protocols our team has in place to proactively address them, I have come to appreciate how wrong I was about our rules being extreme.
…Which brings me to my point: SocketLabs has embraced a pyramid of values with technical security as our foundation, with our users – you – at the very pinnacle. Let’s unpack this.
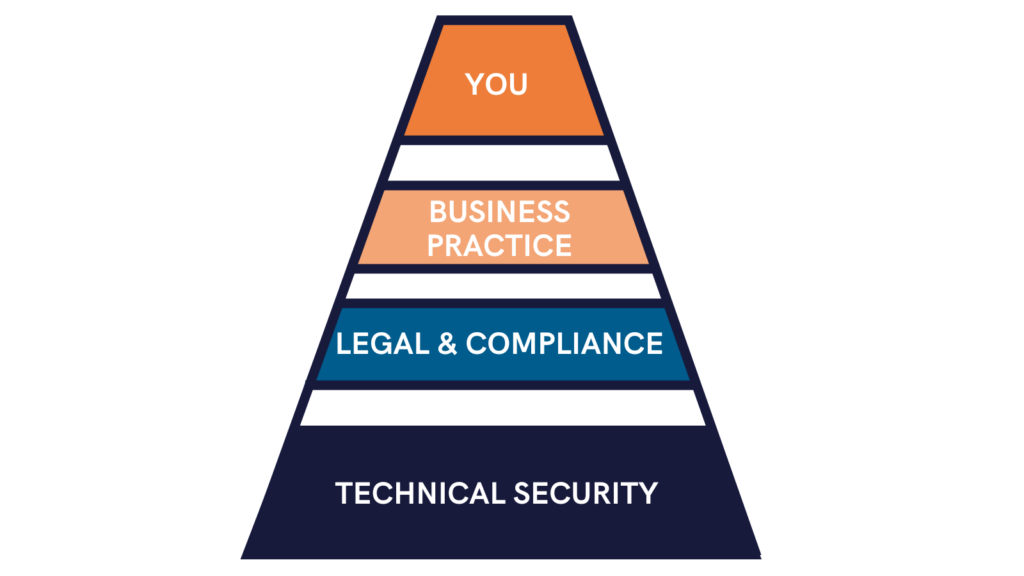
The Foundation of Our Trust Pyramid: Technical Security
The foundation of our trust pyramid is, naturally, technology. We are an email company, after all.
Fundamentally, we believe the best approach to security is multilayered, because any individual layer can become a weak point. A multilayered approach creates a difficult labyrinth to breach and builds resiliency. That’s why our Socket-blue is wrapped around every layer of the pyramid.
Let’s Begin with the Table Stakes
There are a handful of things we consider non-negotiable. Our “table stakes” are the bare minimum for us to reach, so you can always count on these things being a part of our approach to your email security.
- Multifactor Authentication (MFA) for both customers and the internal team
- AES-256 encryption to secure customer data at rest
- Encryption via TLS and HTTPS for data in transit
- Hybrid, automated and team-based suspension for accounts suspected of compromise or malicious activity
- Daily data backups and incremental encrypted recovery for critical infrastructure
- Intrusion Detection Systems (IDS), Endpoint Detection and Response (EDR) and Intrusion Prevention System (IPS) to detect and prevent unauthorized access
- Email’s first ESP to implement MTA-STS, improving secure email delivery
- Let’s Encrypt integration for automated encrypted connections
- Individualized user access controls to allow account admins to get granular about who in their organization is able to access which information in our systems
But Wait, There’s More! We Also Have Notable, Unique Features
The thing I believe best differentiates SocketLabs is our infrastructure, architected with a hybrid, multi-cloud configuration providing redundancy and multi-sender capabilities.
Reliability
Our head of DevOps covered this benefit in greater detail in a blog about our 99.999% reliability.
Tools for Email Security
This multilayered approach isn‘t exclusive to our own actions at SocketLabs. We’ve created multiple cool tools to help our customers and the broader email community succeed at keeping email safe for everybody involved. These include DKIM and DMARC record generators, DNS Lookup, MTA-STS verification, and some handy developer gadgets to enable our email industry.
Additionally, our platform makes sure users and data stay safe, with very robust and feature-specific user permissions to allow you to grant the exact kind of access each individual should have.
Security
Preparedness for potential security incidents is a key focus. We have detailed incident response plans outlining steps for identifying, containing, and mitigating security breaches. Our team regularly reviews and updates these plans to ensure they reflect the latest best practices and threat landscapes.
Additionally, we conduct regular drills to ensure our team is ready to respond swiftly and effectively to any incident, providing transparent status for any potential disruption.
We Also Use Supplemental, External Security Tools
While we’re proud of the strong technical foundation our team created, we also recognize the benefit of adding in external layers.
We use a managed Security Operations Center (SOC) partner to provide the scale and protection of an enterprise while maintaining the flexibility of a startup. We also have a robust KnowBe4 instance providing security training and ongoing employee testing.
Honestly, I know trust means much more when it comes from a third party rather than a self-tooted horn. So, we work with external auditor, A-LIGN, the global leader in security audits, both for regular penetration testing as well as our annual SOC2 audit.
The Core of Our Trust Pyramid: Legal and Compliance
Yes, I mentioned SOC2 for a reason. We’re certified!
Since legalese and compliance are not usually everyone’s favorite reading material, I condensed our top takeaways into a short list:
- SOC 2 Type 2 certified; we’re able to share our Type 3 summary to the public
- GDPR adherence, including Standard Contractual Clauses for affiliated vendors
- CCPA adherence for our California residents, though we follow these standards globally
- CASL adherence, for our Great Northern neighbors
- HIPAA adherence, but as there is no compliance certification, we meet the requirements, including a BAA
- CAN-SPAM adherence, as well as the more recent requirements outlined by major mailbox providers, particularly one-click unsubscribe, separate from CAN-SPAM
For more details on these, check out our deeper dive into why security is serious at SocketLabs.
Want more? Oh, there’s more. Because as I just said, we take security very seriously.
Even More Insurance and Legal Policies
Our last line of defense in our layered approach to business security is an encompassing insurance policy, including cyber liability.
Less formally, SocketLabs deeply understands the significance of personal data privacy, and proudly, always has. In fact, our original privacy policy maintained data-creator control more than a decade before it became a requirement of GDPR.
SocketLabs does not sell, rent or lease its customer lists to third parties.
This core principle remains in our current privacy policy, which has evolved into an even more restrictive and encompassing statement over time. As the technology market continues to evolve—especially with the rise of increasingly complex machine learning—selecting a partner with privacy consideration at their core is crucial to anyone doing business with personal data.
We Stay Vigilant in Allowing People into Our Community
Email is one of the few technologies truly rooted in community. Unfortunately, not every member of a community positively contributes, so the behavior of another customer may positively or negatively impact your email performance.
We decided, much to the chagrin of our revenue team, to act as a (not-terrible) email-style homeowner’s association, and as such, we decline more accounts than we accept through our provisioning process to better protect our customers who do follow the rules.
Our compliance decisions are based on our stringent Acceptable Use Policy (AUP) (not sorry, payday loans and affiliate marketers), so we hope you approve.
What this ultimately leads to is more control over your individual deliverability. Your deliverability will be less negatively affected by bad actors using reputation-impacting shared resources like IPs. Goodbye, shared reputation issues…hello, inbox.
Depending on your role, this may or may not mean much to you, but I can assure you it means a great deal to your go-to-market teams. Fewer concerns about how many people are receiving your email and more focus on how many people are buying the things you’re emailing them about.
This is a good moment to be clear in our hybrid approach to everything we do here. Sure, we have an automated system to help us weed out unacceptable customers, but we blend that machine efficiency with human nuance to reduce the likelihood of nefarious actors slipping in through the cracks. Which is a great segue into the next layer in our trust pyramid…
Business Practices: The Next Layer in our Pyramid
Let’s talk about the people part of the equation a bit.
First, humans: Yes, we have them and they’re not reserved exclusively for our biggest customers. We offer various levels of support from our Customer Success team (who people have quite literally asked us to clone), and every paying customer has access to them in some way.
Though, let’s be honest…sometimes you just don’t want to talk to a human. They’re great if you’ve run into something beyond your control, but if you’re anything like me, you’ll want to exhaust every non-human-contact-required effort before resigning yourself to a support ticket or chat…or phone call! Our handy Help Center was written by our helpful humans (including our most expert in-house deliverability operations geek), so hopefully you’ll find what you need there without much fuss.
Working Together Doesn’t Have to be Painful
Having previously worked at Microsoft, I know how large corporations love their bureaucracy and process for the sake of process. That’s not us. We prefer a more streamlined approach, built around comprehensive cross-functional processes and establishing a single source of truth for information rather than dreaded data silos (shout out to my former manager Michelle for opening my eyes to that!).
We also take every effort to make it as painless as possible to work through our legal and procurement process, something that can frequently be an endless maze. We don’t accept unnecessary risk, but we recognize different customers have different needs, so we work hard to meet them where they are in an efficient and effective way, internally and externally.
We’re Mighty and Capable
Back to our hybrid nature: Another key competitive advantage we have is our size. While we’re smaller than major vendors, SocketLabs has provided email services longer than nearly all of them, continually contributing to the email industry evolution since 2007. We are always working on new things, too. Like…always, wink-wink.
We are proud members and participants of the Messaging, Malware and Mobile Anti-Abuse Working Group (M3AAWG). And, for those who simply cannot get enough email nerdery, we also offer our own monthly virtual round tables under the same closed-session-no-leaks policy as M3AAWG: what happens at the roundtable, stays at the roundtable.
At the Top of the Pyramid – You!
This trust pyramid I’m describing here is a partnership and you’re the all-seeing eye at the top – how lucky!
While we take every precaution to make our environment as secure as possible, this will only work if we have customers and partners behaving similarly.
Here’s what we ask for from all our users:
- Embrace TLS for secure email transmissions.
- Authenticate with DKIM and SPF to verify email authenticity.
- Implement DMARC for robust email protection.
- Access our APIs securely (and, please, never send us your keys.)
- Use multifactor authentication. Always, for everything, we beg of you
- Partner with a trusted ESP for advanced security and compliance…We’re a great choice!
The Rise of First-party Data…and Control
In a world placing an ever-increasing emphasis on data privacy and security with additional legislation in progress in multiple states and around the world, we find the best way to mitigate third-party data’s potential risks, costs, and reliability is to supplement it with first-party data.
In addition to unlocking usable first-party data, we recently expanded our account configuration to enable what can be described as absurdly granular user access control at the parent and child account level. And, over the next few months we will be releasing OAUTH support to enable single sign-on.
Looking Back and Forth
I may have changed my mind about trust being our foundation, but I gained greater appreciation of security enabling trust as our outcome. For any business engagement or even life activity, trust is paramount to shared success. We are confident SocketLabs is a partner you can and should trust, building a sustainable communication foundation to stand the test of time.
While I covered a lot, I’ve actually barely skimmed the surface. If you’re considering working with us to send email or make use of our Spotlight analytics platform, we are total geeks about this kind of thing and could talk about it for days (we won’t, though), so we’d love to get an NDA signed and dive into all things security with you.
Technology continues evolving at a staggering pace. Although it’s impossible to predict exactly where it’s headed, we’re excited to partner with you to chart its new frontiers, from big data and analytics to AI and whatever these machines are capable of next. Our Product folks have a few ideas.