Did you know that the registration information on file for your domain could impact your ability to reach the inbox? This data can also affect your compliance with laws like CAN-SPAM and CASL. The problem is that you likely didn’t think twice about the information you provided during the registration process. You may have even made the mistake of purchasing the privacy service pushed on to you by your registrar that entirely hides your identity. The good news is that this data is really easy to update and taking a few simple steps can ensure it does not negatively impact your business.
WHOIS is the name of the protocol for accessing and retrieving domain registration information. The standard fields returned in response to a WHOIS request include basic information such as name of a registrant and related organization, a physical address, phone number, email address, and more. It also provides basic information like the age of a domain, which can be useful when analyzing validity and reputation of a domain. Domain registrars offer add-on services to hide your personal information from being visible in WHOIS data. This is a major revenue stream for registrars and these add-on’s cost them next to nothing to provide, so many market these services as if they were critical to your purchase.
The technology and sophistication of anti-spam systems is rapidly increasing as the war on spam across the internet continues to wage onward. To better filter malicious email messages, anti-spam architects are grabbing and analyzing any data they can get their hands on. While it’s nothing new to think that filters look at the URLs and domains contained in an email message, it is interesting to think that the WHOIS data can be used to help more accurately filter spam.
Does your organization have accurate WHOIS data published? Check now right here: [ http://whois.icann.org/ ].
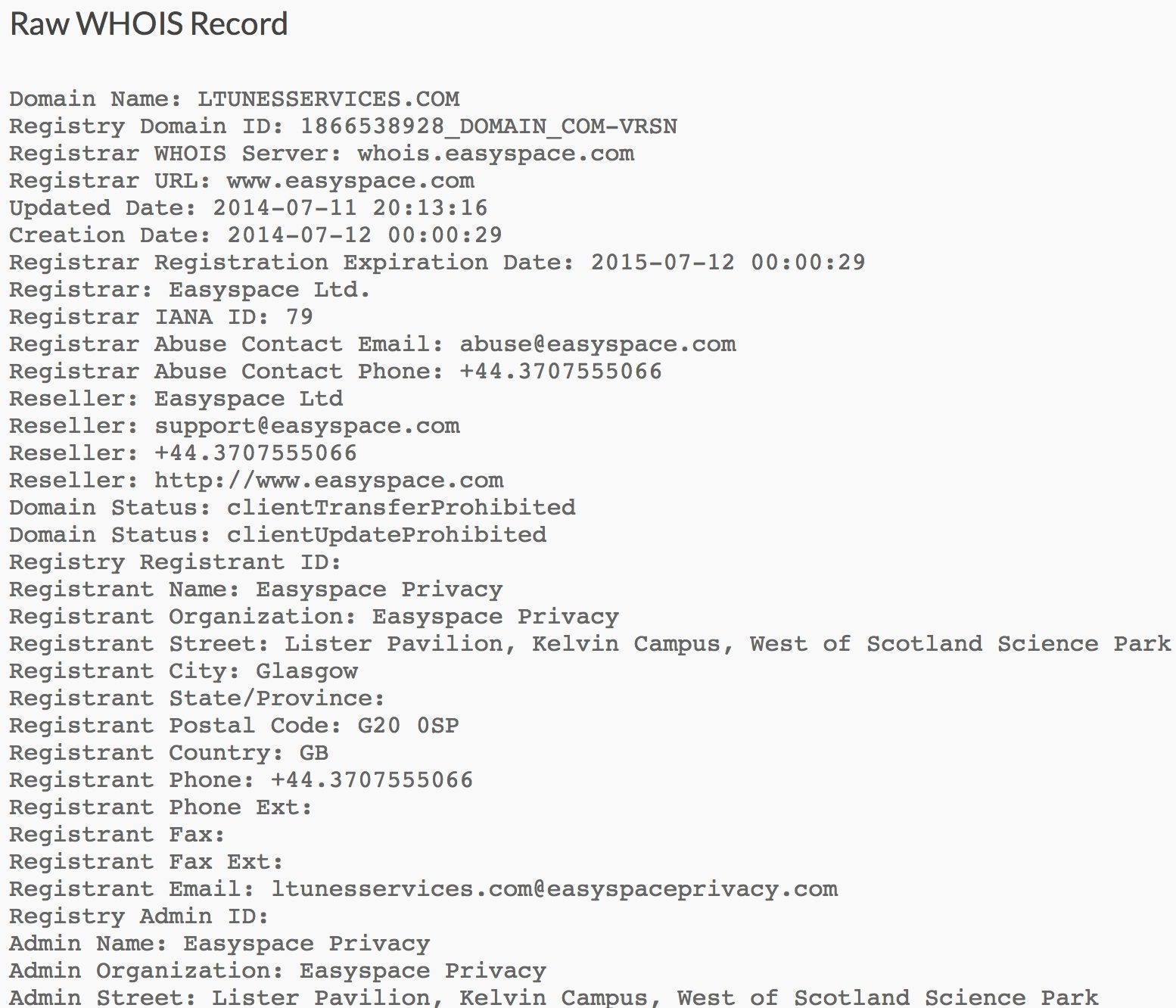
In order for anti-spam filters to benefit from WHOIS data there must be correlation between the data and bad actors to back-up the model. A 2013 study conducted by Dr Richard Clayton of the University of Cambridge concluded that “A significant percentage of the domain names used to conduct illegal or harmful Internet activities are registered via privacy or proxy services to obscure the perpetrator’s identity”. If your organization uses these same privacy and proxy services, it’s likely that it could be causing more of your email message to get filtered to the spam folder.
There is no valid reason for a legitimate organization to hide its identity using these services. If you want to ensure your messages have the best chances of reaching your recipients, stop using these services immediately. This applies to domains used in both your from address field and any domain referenced in your message content.
Having valid WHOIS data on file for your domain is also critical under many anti-spam laws around the world. In the last two years, multiple rulings have been handed down by US judges that imply having generic sender information in combination with a privacy protected domain constitutes a violation of CAN-SPAM. These rulings have been specifically with header falsification policy standards outlined in the CAN-SPAM law:
The appellate court applied CAN-SPAM’s definition of header information and, noting CAN-SPAM’s parallel provision to B&P Code § 17529.5(a)(2), the Court agreed that where the domain names in the emails did not represent a real company and could not be readily traced back to the sender, through available public databases such as WHOIS, such constituted falsification or misrepresentation for purposes of the statute.
Source: Zoobuh v. Better Broadcasting et al
Finally, if reduced inbox placement and federal laws are not enough to make you think twice about sending on behalf of privacy protected domains, the SocketLabs Acceptable Use Policy has always included the limitation that the From address used in your messages must not conceal the identity of the registrant. Violations of our policies may result in the interruption and termination of your services with us here at SocketLabs.







